[ad_1] Read content resources. Above you developed a Code of Virtuous Leadership, but this is really the first step to virtuous decision-making. Sometimes the ethical situations confronting the leader are clearly black and white and application of the Code is
Activity 6- Project Risk
[ad_1] #1 Small to medium businesses are exposed to risks on a daily basis. The impact of these risks could cause a decrease in revenue and/or an increase in expenses. As we all know, every business is subject to risks
3 Week Proposal Presentation Discussion

[ad_1] Use the charts, grafts, excell speadsheets, & pptx info to complete this discussion from the ones completed over the past 3 weeks. The following resources will be used to complete your assignment: Microsoft PowerPoint This week you are creating
Professional Presentation Discussion
[ad_1] post using technologies such as Kaltura, PowerPoint, or any other tool to explain the concepts learned during the week. Minimum of 1 scholarly source Initial Post Instructions This week you learned how to create professional presentations. It is not
Practical connection assignment – INFERENTIAL STATISTICS IN DECISION-MAKING
[ad_1] At our university, it is a priority that students are provided with strong educational programs and courses that allow them to be servant-leaders in their disciplines and communities, linking research with practice and knowledge with ethical decision-making. This assignment
Data Structure and Algorithm heap
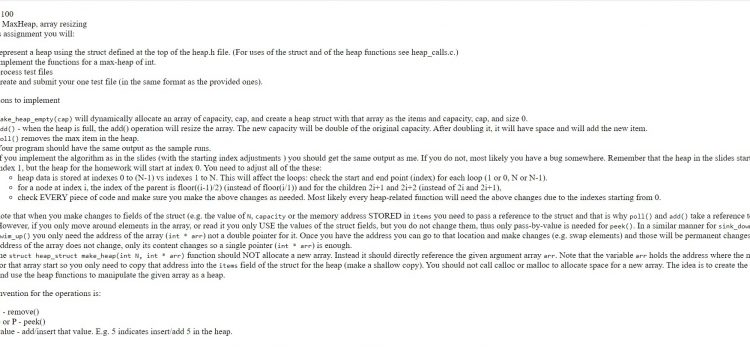
[ad_1] Can someone help me with this? heap.h #ifndef HEAP_H #define HEAP_H struct heap_struct { int* items; int N; // current size int capacity; // array capacity }; // max-heap operations struct heap_struct make_heap_empty(int cap); // assumes arr
Write a summary reading the article. Review NIST Special Publication 800-14 and write a summary of it including extra knowledge you gained in not less than 500 words.
[ad_1] Review NIST Special Publication 800-14 and write a summary of it including extra knowledge you gained in not less than 500 words. Link for the article is given below. https://nam02.safelinks.protection.outlook.com/?url=https%3A%2F%2Ftsapps.nist.gov%2Fpublication%2Fget_pdf.cfm%3Fpub_id%3D890092&data=05%7C01%7Crneupane2%40go.stcloudstate.edu%7Cbc807492e5d445f48e8208daa821994e%7C5011c7c60ab446ab9ef4fae74a921a7f%7C0%7C0%7C638007159503601398%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C3000%7C%7C%7C&sdata=sT8JrSHKW4TkrpAhqO4sAzJxUmfafmcZdnwLJVf%2FQxs%3D&reserved=0 [ad_2]
Network Security
[ad_1] Network Security Project 2 – Tools for 20 Critical Controls Successful deployment of the 20 Critical Controls will require a sophisticated suite of automated tools to support timely operations. This project is designed for you to survey the available
Assignment
[ad_1] Answer the following exercise taken from Ch6. An information system is to be developed to maintain information about assets owned by a utility company such as buildings, vehicles, equipment, etc. It is intended that this will be updatable by
Current Events and Trend Reports: CBI & the Musk Neuralink

[ad_1] Current Events and Trend Reports: CBI & the Musk Neuralink Elon Musk cofounded Neuralink in 2016. He noted his goal is to create a chip that could enable a “brain-computer interface.” On Tuesday 9th, Musk and various senior staffers at