[ad_1] Please choose your paper topic from the following list of topics: 1. Relays A. Current magnetic relay (CMR) B. Potential magnetic relay (PMR) C. Positive temperature coefficient relay (PTC) D. Centrifugal switch 2. Motors A. Split phase motor:
What is it that I want to comprehend to concentrate on moral hacking ?
[ad_1] Ethical hacking is the demonstration of giving and taking PC frameworks to test their security while working with sincere intentions by advance notice the individual who has been compromised. The capacity to morally hack is fundamental for the majority
CTI
[ad_1] Assignment Content Based on the intelligence requirements and risk assessment you completed in the previous project phase, you will determine the collection methods to employ for your chosen organization. You will then deploy the selected tools and methods
Week 3 Assignment
[ad_1] Instructions Assignment #3: In order to complete assignment #3 you will need to answer the below questions. Please complete the questions in a Word document and then upload the assignment for grading. Use examples from the readings, lecture notes
Discussion Reply!!! About 50 words
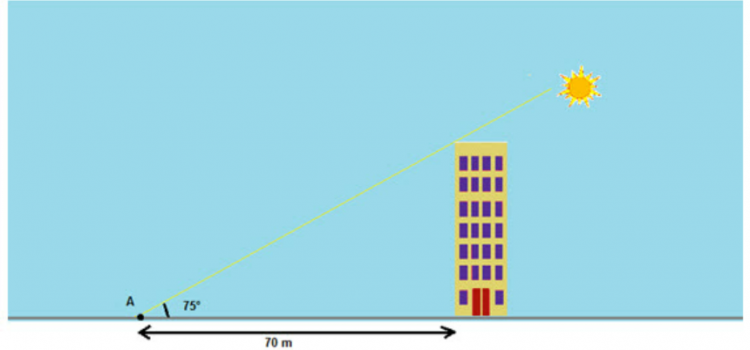
[ad_1] o, I am again going to discuss using the SIN function for calculating height with two known variables. The length of a shadow cast from a building and the calculated angle from the top of the building to the
Engineering Ethics
[ad_1] Write a one-to-two-page paper (not including title page or references, submit as a Word document). Use Times New Roman or Calibri, font size 12, one-inch margins, double-spaced. Don’t forget to cite inside the paper. Be sure to include references
How many people were contacted?
[ad_1] Sampling is an essential element of modern quality management. However, the reason sampling works is that quality managers ensure that the selected sample is representative of the overall population of goods or services being controlled. How do managers assess
Project: Threat Intelligence Requirements
[ad_1] Establishing threat intelligence goals and requirements will help the threat intelligence team to better allocate and utilize its resources and fine-tune the data types, tools, and methods that will produce the most relevant and useful intelligence about the
Discussion Reply!!! About 50 words
[ad_1] The Cosine Rule is used in triangles where one is trying to relate all three sides to one angle. If you need to find the length of a side, you need to know the other two sides and
2 questions
[ad_1] 1. Airport Descriptions To prove your worth as the director of your chosen airport, you need to demonstrate an understanding of the national airport system and the different types of airports. Briefly describe the roles of a commercial services