[ad_1] You will conduct a literature review (scholarly sources only) on Information Governance. You will determine how researchers have attempted to examine that issue by collecting data (you are not collecting data; just reporting on prior research). As you read
Mid-Term – Security Architecture & Design
[ad_1] Icanread System, Inc. is an advertising agency that specialize in selling ad spaces in their parent company’s magazine. Icanread Systems, Inc. manages an online database that allows their customers to upload and pay for their business ads for
Practical Connection Assignment – Security Architecture & Design
[ad_1] At UC, it is a priority that students are provided with strong education programs and courses that allow them to be servant-leaders in their disciplines and communities, linking research with practice and knowledge with ethical decision-making. This assignment
Identify at least two ways in which hackers gather information about companies. What can companies do to limit this access, specifically to the ways you have identified?
[ad_1] Identify at least two ways in which hackers gather information about companies. What can companies do to limit this access, specifically to the ways you have identified? Which type of information can be gathered with enumeration? How and why
Discussion
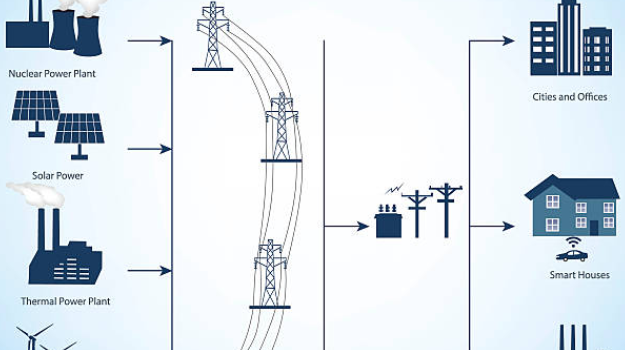
[ad_1] The Power Grid and Big Data Contains unread posts (Clipart from MS Office) The electric-utility business is going through a major business process reengineering (BPR), stemming from technology improvements, economic forces, and public awareness. The electricity sector is
Backup strategies
[ad_1] Assume you are a security professional. You are determining which of the following backup strategies will provide the best protection against data loss, whether from disk failure or natural disaster: Daily full server backups with hourly incremental backups Redundant
Business Intelligence Assignment
[ad_1] Complete the following assignment in one MS word document: Chapter 7 –discussion questions #1-4 (page # 456) & Application Case 7.8 on page # 447. Please answer the two case questions on page 450, integrating concepts and examples from
Consultant Report
[ad_1] Following the press release by VITA [access it here Links to an external site.], you have been retained as a consultant by the office of the Commonwealth of Virginia Secretary of State for Technology. You are tasked with the
Write a Business Proposal for Minimizing a Data and Security Breach
[ad_1] Scenario The HIT Innovation Steering Committee within an organization is proactively looking at data breaches of other organizations to assist them with minimizing the risk to their data security and privacy. As an intern at this organization, you
paper
[ad_1] week 5 Assignment – Database Modeling and Normalization Overview Imagine that you work for a consulting firm that offers information technology and database services. Part of its core services is to optimize and offer streamlined solutions for efficiency.